8+ vector memory exhausted r
Programs are started at a fixed address and the program can use a single instruction to make most memory references. For each constraint of T that is a struct type R contains SystemValueType.

An Adaptable Water Soluble Molecular Boat For Selective Separation Of Phenanthrene From Isomeric Anthracene Journal Of The American Chemical Society
Where this Specification uses technical terminology defined in the Glossary or otherwise that refer to enabling technologies that are not expressly set forth in this Specification those enabling technologies are EXCLUDED from the Scope of this Specification.
. The lack of an efficient anti-tumor T cell response contributes to the failure of anti-PD1 therapy. Char uchar short ushort int uint long ulong float or double followed by a literal value n that defines the number of elements in the vector. The Artificial Bee Colony ABC algorithm is a swarm based meta-heuristic algorithm that was introduced by Karaboga in 2005 Karaboga 2005 for optimizing numerical problemsIt was inspired by the intelligent foraging behavior of honey bees.
742 Iterating an. Immunotherapy using immune checkpoint molecule blockade has limited effectiveness in some tumors due to the presence of exhausted CD8 T. Attached to this tensor is a number representing real value scale that is used to convert the 8 bit number to a real value in the following way.
The GNU Arm Embedded Toolchain targets the 32-bit Arm Cortex-A Arm Cortex-M and Arm Cortex-R processor families. RealValue integerValue scale. There is good support in R see Matrix package for eg for sparse matrices.
Supported values of n are 2 3 4 8 and 16 for all vector data types. They profiled histone modifications in tumor-infiltrating CD8 T cells using. Keep all other processes and objects in R to a minimum when you need to make objects of this size.
Allowed memory size of X bytes exhausted tried to allocate Y bytes Raise PHPs memory limit in phpini. 74 Iterating over a one-dimensional vector. The GNU Arm Embedded Toolchain is a ready-to-use open-source suite of tools for C C and assembly programming.
Tag is the anchor name of the item where the Enforcement rule appears eg for C134 it is Rh-public the name of a profile group-of-rules type bounds or lifetime or a specific rule in a profile type4 or bounds2 message is a string literal Instruct. The statistical software packages used include R v362 and Prism 8 GraphPad. Let R be a set of types such that.
For each constraint of T that is a type parameter R contains its effective base class. Most effective is to represent a third or fourth numeric quantity on a scatterplotonce the two position cues have been exhausted. This function is lazy.
Passive immunotherapy using monoclonal antibodies and donor T cells is effective in some types of cancer but despite extensive research. Memory_limit 64M. Second approximately 8 of the populationmost of whom are men.
Program units compiled using either -mcmodelmedium or -fpic require additional instructions to reference memory. Tag is the anchor name of the item where the Enforcement rule appears eg for C134 it is Rh-public the name of a profile group-of-rules type bounds or lifetime or a specific rule in a profile type4 or bounds2 message is a string literal Instruct. Using electronic health records data from the All of Us Research Program we show that higher daily step counts in data collected over several years of Fitbit fitness tracker use were associated.
Scale is a 32 bit floating point with value greater than zero. Examined underlying mechanisms associated with accumulation of terminally differentiated exhausted CD8 T cells in tumors. Each rule guideline suggestion can have several parts.
A tensor of 8 bit signed integers that represent real numbers. That is it is guaranteed to return in Θ1 time and use Θ1 additional space and flt will not be called by an invocation of filter. The algorithm is specifically based on the model proposed by Tereshko and Loengarov 2005 for the foraging behaviour of.
Phenotyping of T cell memory. The effect on performance. The pointer will be properly aligned and non-null.
If the data is passed as a Float32Array and changes to the data will change the tensorThis is not a feature and is not supported. Since MediaWiki 123 you may end with a wiki with most of the Vector-specific skin styles like sidebar placed at the end of the page. For each constraint of T that is a delegate type R contains its.
2121 Data and memory structures for. In computing a denial-of-service attack DoS attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a networkDenial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an. Customers who have exhausted their t2micro or t3micro depending on the Region Free Tier usage can still benefit from the T4g free trial.
The magnitude of the SARS-CoV-2-specific CD4 and CD8 memory T cell response is typically around 05 and 02 of the repertoire respectively 63 although a characteristic feature is. Here the authors show a potential strategy to improve the therapeutic effects of anti-PD-1. Maximum amount of memory a script may consume 32MB.
Consumes the Box returning a wrapped raw pointer. After calling this function the caller is responsible for the memory previously managed by the BoxIn particular the caller should properly destroy T and release the memory taking into account the memory layout used by BoxThe easiest way to do this is to convert the raw pointer back. The structure of this document.
For clarity enabling technologies not disclosed with particularity in this Specification eg. Iteratorsfilterflt itr Given a predicate function flt and an iterable object itr return an iterable object which upon iteration yields the elements x of itr that satisfy fltxThe order of the original iterator is preserved. Downloads See Arm GNU Toolchain Downloads to access the latest release of the toolchain.
An overview of the latest advances in cancer immunotherapy. Available since NNAPI feature level 3. Each rule guideline suggestion can have several parts.
For each constraint of T that is an enumeration type R contains SystemEnum. The structure of this document. Use gc to clear now unused memory or better only create the object you need in one session.
An ebook short for electronic book also known as an e-book or eBook is a book publication made available in digital form consisting of text images or both readable on the flat-panel display of computers or other electronic devices. A tfTensor object represents an immutable multidimensional array of numbers that has a shape and a data type. Intel Advanced Vector Extensions 512 AVX-512 is a set of new CPU instructions available on the latest Intel Xeon Scalable processor family that can accelerate performance for workloads and usages.
Although sometimes defined as an electronic version of a printed book some e-books exist without a printed equivalent. For performance reasons functions that create tensors do not necessarily perform a copy of the data passed to them eg. 741 Iterating a known function.
Once you are proficient with Bison you can use it to develop a wide range of language parsers from those used in simple desk calculators to complex. The CD19-22BBz-CAR was encoded by a self-inactivating lentiviral vector. The vector data type is defined with the type name ie.
Bison is a general-purpose parser generator that converts an annotated context-free grammar into a deterministic LR or generalized LR GLR parser employing LALR1 IELR1 or canonical LR1 parser tables. The medium memory model allows for larger than 2GB data areas or bss sections.

Cytotoxic T Cell Overview Thermo Fisher Scientific Us
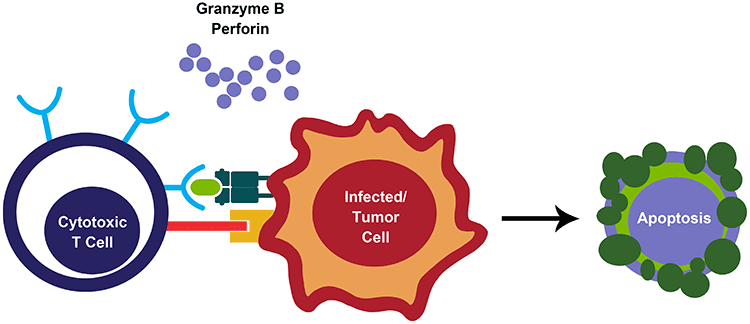
Cytotoxic T Cell Overview Thermo Fisher Scientific Us
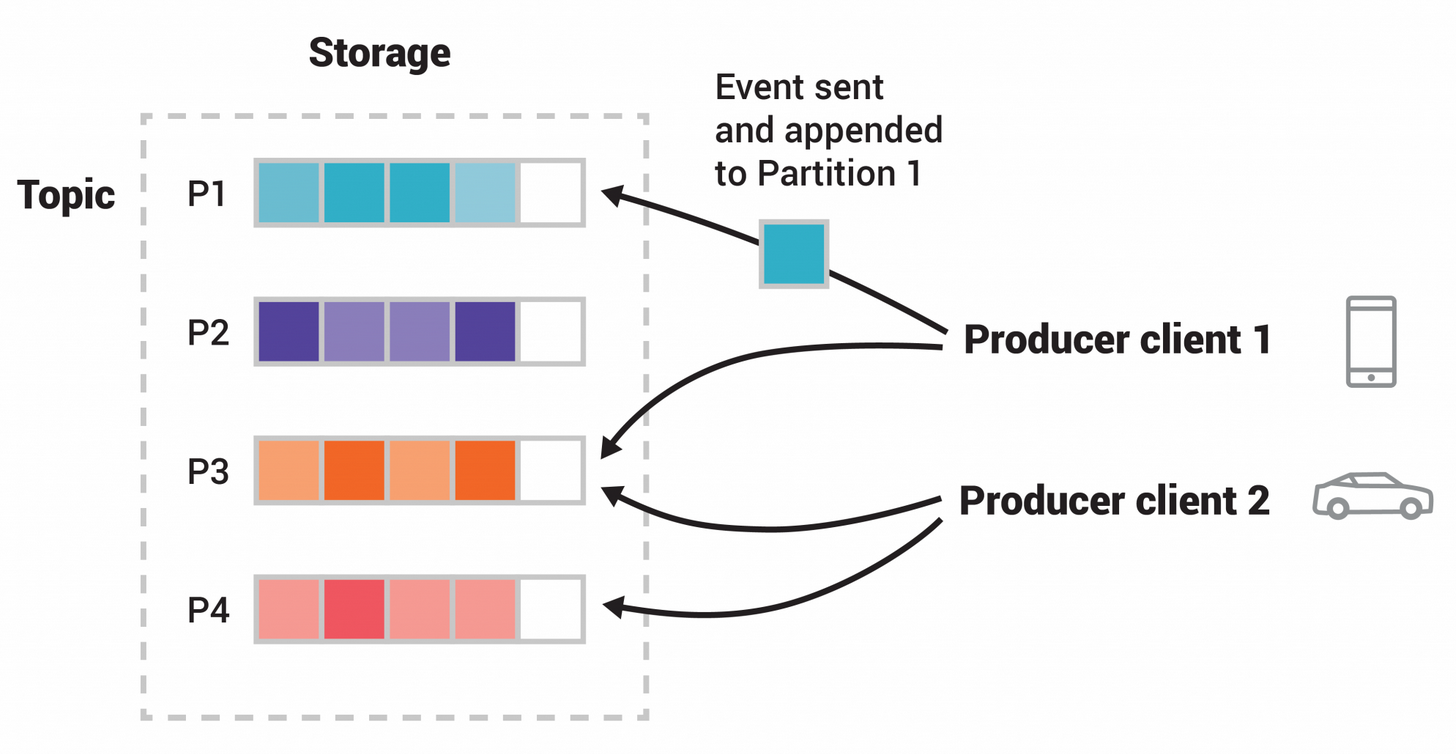
Apache Kafka
Error Memory Exhausted Limit Reached Issue 192 R Spatialecology Landscapemetrics Github

Understanding Idiosyncratic Toxicity Lessons Learned From Drug Induced Liver Injury Journal Of Medicinal Chemistry
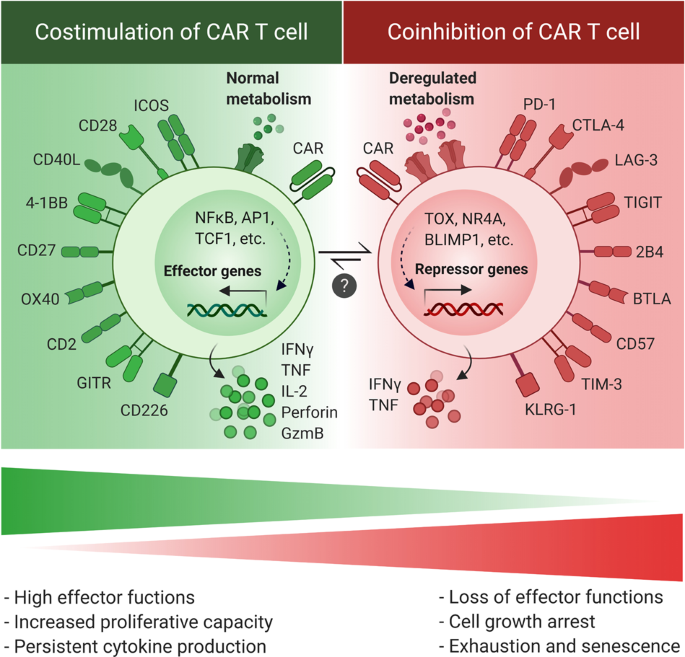
Counteracting Car T Cell Dysfunction Oncogene

Error Vector Memory Exhausted Limit Reached Guide To Fixing This

Dataframe R Vector Memory Exhausted Limit Reached Stack Overflow
Error Memory Exhausted Limit Reached Issue 192 R Spatialecology Landscapemetrics Github

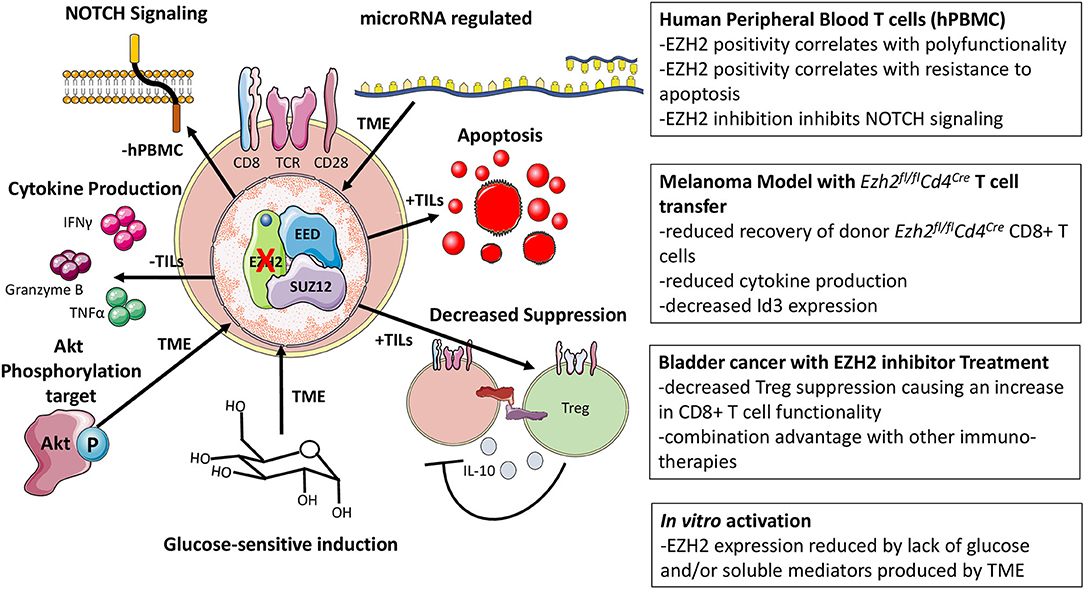
Frontiers Ezh2 As A Regulator Of Cd8 T Cell Fate And Function
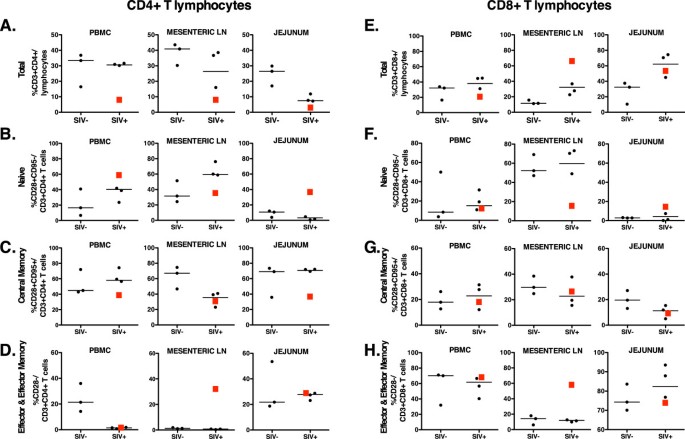
Prolonged Tenofovir Treatment Of Macaques Infected With K65r Reverse Transcriptase Mutants Of Siv Results In The Development Of Antiviral Immune Responses That Control Virus Replication After Drug Withdrawal Retrovirology Full Text

An Adaptable Water Soluble Molecular Boat For Selective Separation Of Phenanthrene From Isomeric Anthracene Journal Of The American Chemical Society

Understanding Idiosyncratic Toxicity Lessons Learned From Drug Induced Liver Injury Journal Of Medicinal Chemistry

Programmed Cell Death Protein Ligand 1 Silencing With Polyethylenimine Dermatan Sulfate Complex For Dual Inhibition Of Melanoma Growth Acs Nano
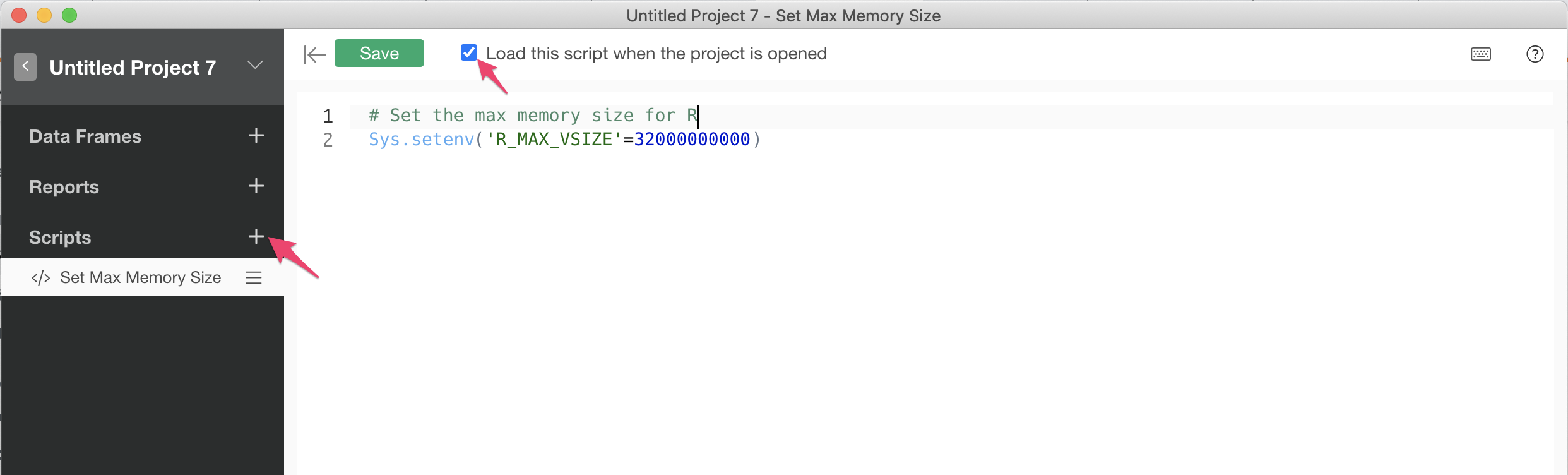
Error Vector Memory Exhausted Limit Reached Issues Exploratory Community
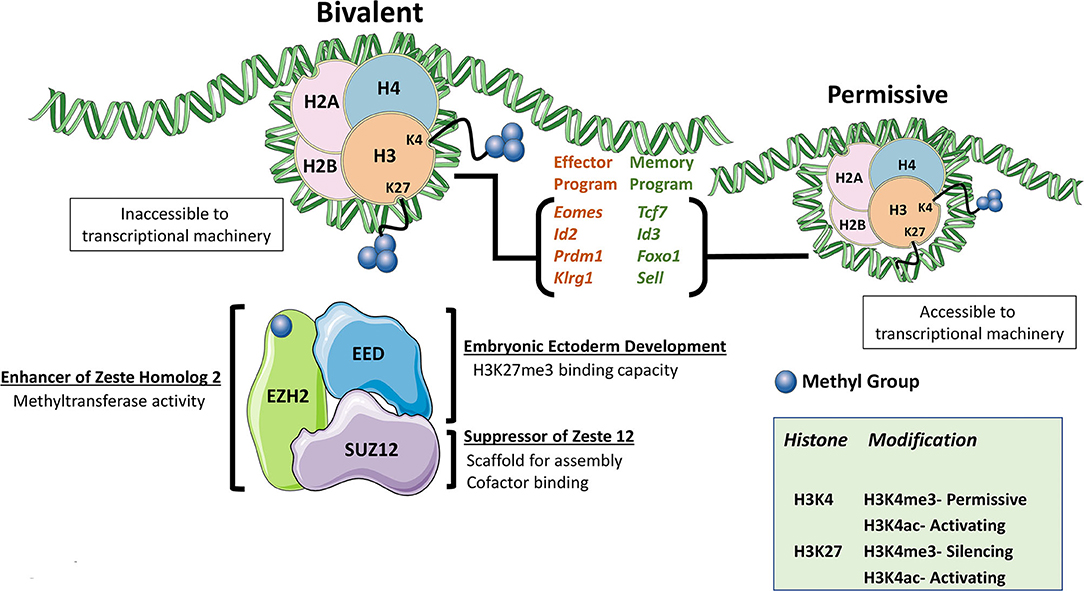
Frontiers Ezh2 As A Regulator Of Cd8 T Cell Fate And Function

Revving The Car Combination Strategies To Enhance Car T Cell Effectiveness Sciencedirect